The Importance of Protected Text in the Digital Age
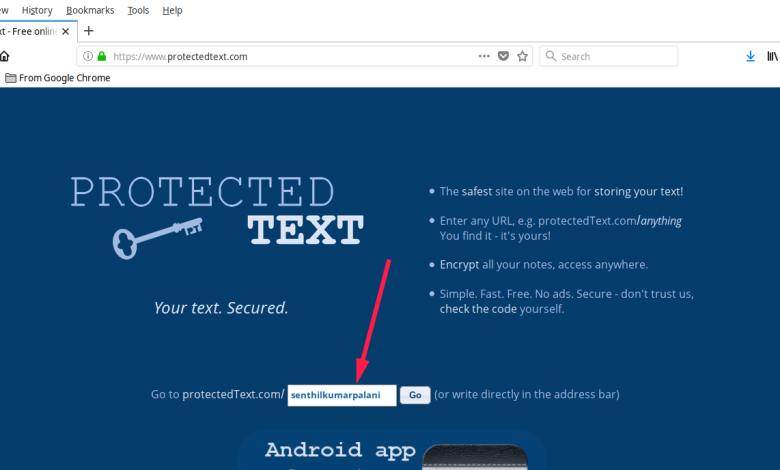
Table of Contents
ToggleIn today’s digital landscape, safeguarding sensitive information has become more critical than ever. Whether you’re a business professional, a student, or an individual concerned with privacy, understanding and utilizing “protected text” can significantly enhance your data security. This blog post will explore the concept of protected text, its benefits, methods for securing text, and best practices for maintaining its integrity.
What is Protected Text?
Protected text refers to any text-based content that is secured against unauthorized access, modification, or deletion. This protection can be achieved through various methods, such as encryption, password protection, or using specialized software designed to keep your text confidential. The primary goal of protected text is to ensure that only authorized individuals can view or manipulate the information, thereby safeguarding privacy and security.
Why is Protected Text Essential?
- Privacy: In an era where data breaches are common, keeping your information private is crucial. Protected text ensures that your sensitive information remains confidential, accessible only to those with the necessary permissions.
- Security: For businesses, protecting text can prevent unauthorized access to critical documents, thereby avoiding potential financial and reputational damage.
- Compliance: Many industries have stringent regulations regarding data protection. Utilizing protected text helps in complying with these regulations, thus avoiding legal repercussions.
- Peace of Mind: Knowing that your information is secure provides peace of mind, allowing you to focus on other important tasks without worrying about data breaches.
Methods to Protect Text
There are several methods available to protect your text, each with its own set of advantages:
1. Encryption
Encryption converts your text into an unreadable format that can only be deciphered with a specific key. This method is highly effective in securing sensitive information.
- Symmetric Encryption: Uses the same key for both encryption and decryption, making it faster but requiring secure key management.
- Asymmetric Encryption: Uses a pair of keys – a public key for encryption and a private key for decryption, enhancing security but being computationally intensive.
2. Password Protection
Password protection involves securing your text with a password. Only individuals who know the password can access the content. This method is commonly used in applications like Microsoft Word and Adobe PDF.
3. Secure Software
Various software tools are designed to protect text. These tools often offer additional features such as automatic backups, user access controls, and audit logs, providing comprehensive protection for your text.
How to Create Protected Text
Creating protected text is straightforward, and there are multiple tools and techniques you can use:
Using Word Processing Software
Most word processing software, such as Microsoft Word, offers built-in features to protect your documents.
- Encrypt with Password: In Microsoft Word, go to File > Info > Protect Document > Encrypt with Password. This ensures that only users with the password can open the document.
- Restrict Editing: This feature allows you to limit the changes that others can make to your document, providing an additional layer of protection.
Using PDF Editors
PDF editors like Adobe Acrobat provide robust options for securing your text.
- Password Protection: In Adobe Acrobat, go to File > Protect Using Password. This ensures that only users with the password can access the PDF.
- Certificate Encryption: This method uses digital certificates to encrypt your PDF, ensuring that only those with the corresponding certificate can access it.
Online Tools
Several online tools can help you create protected text. These tools are often free and easy to use. Examples include:
- ProtectedText.com: A simple, secure online notepad with encryption, allowing you to store notes safely.
- LockNote: A lightweight application that lets you save your text with password protection, ensuring your notes are secure.
Best Practices for Using Protected Text
- Use Strong Passwords: Ensure that your passwords are strong and unique. Avoid using easily guessable passwords like “123456” or “password”. A strong password typically includes a mix of letters, numbers, and special characters.
- Keep Software Updated: Always use the latest version of your software to benefit from the latest security updates. Regular updates often include patches for security vulnerabilities.
- Backup Regularly: Regularly back up your protected text to prevent data loss. Use secure backup solutions that offer encryption to ensure your backups are also protected.
- Educate Yourself: Stay informed about the latest trends and practices in data protection to enhance your security measures. Understanding potential threats can help you take proactive steps to safeguard your text.
Common Use Cases for Protected Text
Protected text is used across various domains to ensure the confidentiality and integrity of information. Some common use cases include:
1. Business Documents
Companies often use protected text to safeguard sensitive business documents such as contracts, financial records, and strategic plans. Ensuring that these documents are protected helps prevent unauthorized access and potential misuse.
2. Academic Research
Researchers use protected text to secure their work, ensuring that their findings are not accessed or stolen before publication. This is crucial in maintaining the integrity of their research and preventing intellectual property theft.
3. Personal Information
Individuals use protected text to keep personal information like diaries, passwords, and personal notes secure. Protecting personal information helps maintain privacy and prevents identity theft.
Conclusion
In conclusion, protected text is an essential tool for anyone who values privacy and security. By understanding the different methods of creating protected text and following best practices, you can ensure that your sensitive information remains confidential and secure. Whether you are protecting business documents, academic research, or personal information, utilizing protected text will give you the peace of mind that your data is safe from unauthorized access.
Remember, in today’s digital world, taking proactive steps to protect your text is not just an option; it’s a necessity. Stay informed, stay secure, and make the most out of the tools available to protect your text effectively. By incorporating protected text into your data security strategy, you can safeguard your information and maintain the privacy and integrity of your data.